SSH server can be configured to authenticate using other methods than password, such as private/public keys, or “trusted” known hosts. It can be set up easily on any Linux distribution to login SSH without (typing) password.
.
Setup
Most of Linux, e.g. Ubuntu (Windows/Cygwin: Git Bash), has built-in OpenSSH daemon and we can configure it to be connected by SSH client without password (also known as: passwordless SSH) by below steps:
.
Create public and private keys
using ssh-keygen on local-host (preferred option “-C” with email, e.g “ducquoc.xx@gmail.com”):
ducquoc@server:~ $ ssh-keygen -t rsa -C ducquoc.vn@gmail.com
Generating public/private rsa key pair.
Enter file in which to save the key (/home/ducquoc/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/ducquoc/.ssh/id_rsa.
Your public key has been saved in /home/ducquoc/.ssh/id_rsa.pub.
The key fingerprint is:
f6:61:a8:27:35:cf:4c:6d:13:22:70:cf:4c:c8:a0:23 ducquoc@server
(lưu ý nếu không muốn dùng email làm ID, thì ko dùng option “-C“, sẽ mặc định username@hostname
$ ssh-keygen -t rsa
)
.
Copy content of the public key to remote-host
Git hosting services
support “SSH key” for Git over SSH:
BitBucket: https://support.atlassian.com/bitbucket-cloud/docs/set-up-an-ssh-key/#Step-3.-Add-the-public-key-to-your-Account-settings
GitLab: https://subscription.packtpub.com/book/application-development/9781783986842/2/ch02lvl1sec20/adding-your-ssh-key-to-gitlab
GitHub: https://docs.github.com/en/github/authenticating-to-github/connecting-to-github-with-ssh/adding-a-new-ssh-key-to-your-github-account
Hosted GitLab: https://linuxhint.com/add-and-configure-ssh-key-on-gitlab/
General Remote Host
we can copy by using ssh-copy-id script
ducquoc@server:~ $ ssh-copy-id -i ~/.ssh/id_rsa.pub remoteuser@remote-host
remoteuser@remote-host’s password:
Now try logging into the machine, with “ssh ‘remoteuser@remote-host'”, and check in:.ssh/authorized_keys
to make sure we haven’t added extra keys that you weren’t expecting.
.
Login to remote-host without entering the password
ducquoc@server:~ $ ssh remoteuser@remote-host
Last login: Fri Dec 16 17:22:33 2009 from 192.168.22.84
(If successful, you will be on remote-host here, without typing any password)
remoteuser@remote-host:~ $ exit
.
More info
The command ssh-keygen -t rsa initiated the creation of the key pair.
No passphrase was entered (Enter key was pressed instead). You can add option
-P ""
to create empty password for the key immediately (so that user doesn’t have to press Enter 3 times)
The private key was saved in .ssh/id_rsa . This file is read-only and only for you. No one else must see the content of that file, as it is used to decrypt all correspondence encrypted with the public key.
The public key is save in .ssh/id_rsa.pub .
In this case, the content of file id_rsa.pub is
ssh-rsa AAAAB3Nz...blah.blah...Q0d+1U2WVdBWQM= ducquoc@server
(It is one line in length.)
Its content is then copied in file .ssh/authorized_keys of the system you wish to SSH to without being prompted for a password.
The example shown here generated keys on hmsdevserver by user hmsdev. If the public key generated, file .ssh/id_rsa.pub , was copied to your account, file .ssh/authorized_keys on the remote host, then user ducquoc@server is allowed to SSH into your remote account (remoteuser) on remote host (remote-host) without the use of a password.
To summarize, a personal private/public key pair is generated using the ssh-keygen command. The public key is then copied onto a remote systems’ .ssh/authorized_keys file. And you can now SSH to the remote systems’s account without the use of a password.
We also have some alternative commands for every steps (1, 2, 3) :
$ ssh-keygen -t ecdsa -C ducquoc@yopmail.com
(ECDSA algorithm, then the public/private key is id_ecdsa.pub/id_ecdsa )
$ cat .ssh/id_rsa.pub | ssh remoteuser@remote-host ‘cat >> .ssh/authorized_keys’
(copy content of id_rsa.pub to authorized file on remote-host, without using ssh-copy-id)
$ ssh remote-host -l remoteuser
(using option -l to specify username on remote host, same with remoteuser@remote-host)
.
Bonus: After adding SSH Key to git host (BitBucket, GitLab, GitHub) – you can check git connection with:
$ ssh -vT git@gitlab.com
.
Troubleshooting
Things to check when it does not work after those steps:
Check version of SSH client
$ ssh -V
Check SSH authorized store
$ ls -lt ~/.ssh
Check content of authorized file:
$ cat .ssh/authorized_keys
Check SSHd config files
$ ls /etc/ssh
Check script ssh-copy-id
$ whereis ssh-copy-id
Check authentication log
$ tail -f /var/log/auth.log
If the Linux system doesn’t have ssh-copy-id script, use the alternative command above, like this one:
$ cat .ssh/id_rsa.pub | ssh remoteuser@remote-host ‘cat >> .ssh/authorized_keys’
Make sure to enable SSH key authentication, in the file /etc/ssh/sshd_config (NOT ssh_config )
RSAAuthentication yes
PubkeyAuthentication yesPermitRootLogin yes
(Restart SSH daemon after changing sshd_config
$ /etc/init.d/ssh restart
)
Some versions of SSH required strict permissions (700 for ~/.ssh , 640 or 600 for ~/.ssh/authorized_keys on both hosts)
$ sudo chmod 700 ~/.ssh
$ sudo chmod 600 ~/.ssh/authorized_keys
Some old versions of SSH can have ~/.ssh/authorized_keys2 instead of ~/.ssh/authorized_keys .
.
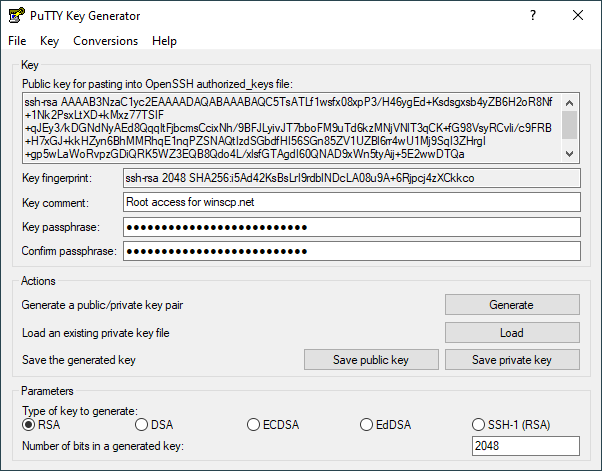
EDITED: Redmond (Windoze) users: có thể dùng GitBash hoặc PuTTyGen để sinh cặp key SSH
+ Git Bash: thường cài Git for Windows đã có sẵn Git Bash, thì nên sử dụng Git Bash – đã có MingW/Cygwin – để generate như hướng dẫn ở trên, vì GitBash có tích hợp sẵn ssh-agent tự start.
https://www.sitecuatui.com/tao-ssh-key-bang-puttygen/
Sau đó nhớ thêm private key vào SSH-agent của PuTTy là Pageant :
nếu ko thêm vào SSH-Agent sẽ phải manually chỉ tới private key ở phần PuTTy config SSH -> Auth
./.

Duc’s rant: This tip is a very common in Linux/Unix users, but I have to take note for quick reference every time. One thing that bugged me is that I had to Google it again after changing the workplace, since I had forgotten to copy it from old workplace’s wiki…
Pingback: Hadoop cluster setup | DucQuoc's Blog
Duc’s rant continued…
One of my co-workers has agreed to copy some of my posts in the old wiki for me, yet it is 2 months and I haven’t heard anything about that :-(
. . . guess it can’t be helped afterall . . .
Pingback: Install PostgreSQL Database | DucQuoc's Blog
Pingback: Secure online info | DucQuoc's Blog
Pingback: Linux Basic Commands | DucQuoc's Blog
(Update 2023)
It’s recommend to use ECDSA (DON’T user `DSA`) or ED25519 in newer version of OpenSSH (7.0 and higher)
“`
ssh-keygen -t ecdsa -C ducquoc@users.noreply.github.com
ssh-keygen -t ed25519 -C ducquoc-private.co@yopmail.com
“`
The generated keys will be stored in `$HOME/.ssh/` by default. This can help things easier to use multi emails (work/opensource/personal) , rather than custom “Host” in SSH config, or manual in each Git repository.